Cyber-crooks pushing ransomware through Google results
Ransomware, that nasty malware that can scramble all of your personal files and demand a ransom to get them back, can infect a device in a number of different ways. But perhaps most commonly it’s because someone was tricked into opening up an email attachment they shouldn’t have.
But ransomware crooks are always looking for more opportunities, and using the Internet’s biggest search engine, Google, to lure potential victims to booby trapped websites is one such opportunity. And that’s exactly how the Gootkit family of malware is trying to infect devices according to a new report from SophosLabs.
But exploiting Google to deliver your malware is not without its challenges. To use this method of attack, you actually have to rank a malicious webpage in Google, and it needs to rank well (i.e. the top few results) and you need to rank it for search terms that people are actually searching for. That’s a little more effort that merely creating a website, placing your booby trap and hoping for the best, as any Internet marketer will tell you. But the crooks behind Gootkit are cleverly gaming the Google algorithm, and here’s how.
Hack a lot of other websites
Brand new websites don’t rank well in Google, and if they’re just going to be serving malware to passing visitors, well, Google probably isn’t going to rank the site at all. The crooks need established, content-rich and respected websites to plant their malware – websites that are more likely to appear in Google. So the first step is to gain unauthorised access to such websites to place those booby traps.
Sponsored Content. Continued below...
The booby trap is design to attract visitors from Google who searched for specific keywords…
Next, the booby trap planted on the hacked website generates fake content that is designed to appear in Google search results when a Google user types in certain keyword phrases. The idea is that someone using Google types in a certain question or phrase, and the fake content generated by the hacked website appears as the top search result. This example provided by SophosLabs demonstrates how this works –
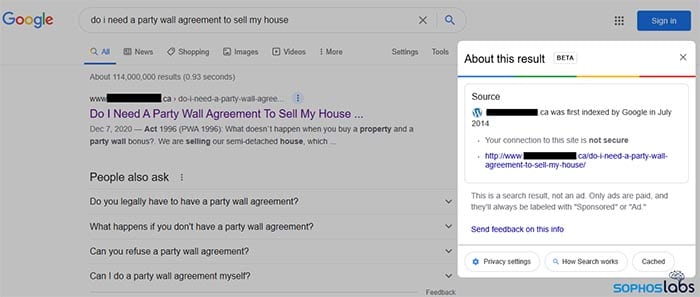
The Google user has typed in “do I need a party wall agreement to sell my house“. The top search result looks like a perfect match. But the website is actually a neo-natal website in Canada, and has nothing to do with real estate law. The site was compromised by the crooks and made to generate fake content related to the above keyword phrase. It now appears at the top of Google’s search result and the Google user is likely to click on it…
The fake forum.
But the crooks need a victim to do more than click on a Google search result. They also need the victim to agree to download the malware. And this is where the fake forum comes into play. When the Google visitor clicks the search result, the hacked website identifies that the visitor is coming from Google, and presents them with what appears to be a forum where a forum user is asking the same question the visitor typed into Google. As per the below image.
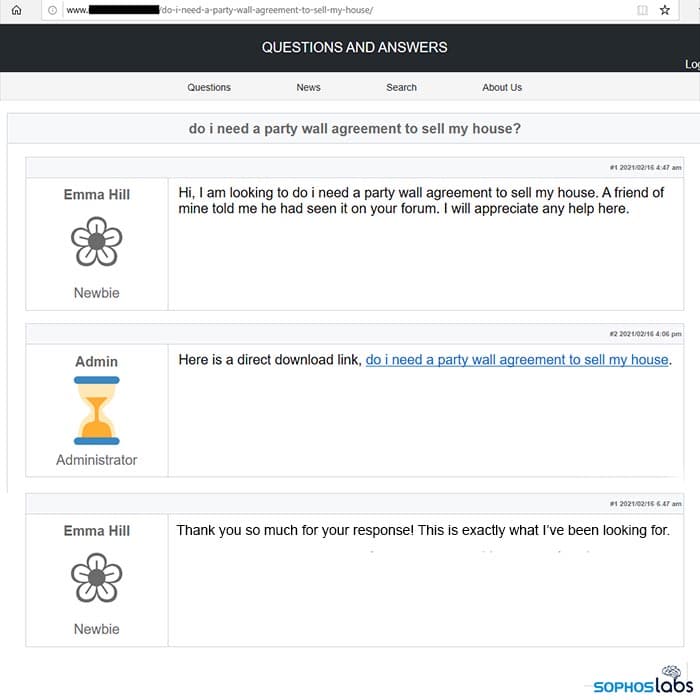
The apparent site administrator then replies, offering a download link, which the forum user thanks them for, claiming it was “exactly what [they’ve] been looking for”. The plan is to lure the Google visitor into clicking that same download link, believing it to answer the question they had originally typed into Google.
Only, of course, it isn’t answering anything. It’s a malicious JS file that ultimately leads to a nasty malware infection.
Sponsored Content. Continued below...
You can see how this ruse may be convincing. From the victim’s perspective. They typed a question into Google, clicked a result at (or near) the top of the results which looked like a good match, and then downloaded a file posted by the site administrator of that website, to which other forum users thanked them for.
The victim may not realise that the whole thing was fake. They may not realise that the forum wasn’t real, and the owners of the website most likely have no idea the fake forum even exists on their site. The victim won’t realise that the “site administrator” isn’t real, and nor is the forum user asking the same question. It’s all artificially generated content on a hacked website serving one single purpose; to trick the victim into downloading malicious files.
Always remember to have reliable security software installed at all times, and always be on the lookout for suspicious search results. In the example above, a neo-natal website offering real estate advice would certainly be a red flag, coupled with the all-too-convenient search results and download link.
Keep up-to-date with all our latest articles. Follow us on Facebook, Instagram and Twitter.
Continued below...
Thanks for reading! But before you go… as part of our latest series of articles on how to earn a little extra cash using the Internet (without getting scammed) we have been looking into how you can earn gift vouchers (like Amazon vouchers) using reward-per-action websites such as SwagBucks. If you are interested we even have our own sign-up code to get you started. Want to learn more? We discuss it here. (Or you can just sign-up here and use code Nonsense70SB when registering.)
Become a Facebook Supporter. For 0.99p (~$1.30) a month you can become a Facebook fan, meaning you get an optional Supporter Badge when you comment on our Facebook posts, as well as discounts on our merchandise. You can subscribe here (cancel anytime.)
