Crooks use leaked passwords in the “you’ve watched adult content” extortion scam
Email scammers are using passwords obtained from large scale security breaches to scare victims into thinking they’ve been caught watching sensitive or adult content.
In the past we have reported on a particularly audacious and potentially convincing email scam which claims to have video of the email recipient (the victim) watching adult content.
In the email, the scammer claims to have installed malware onto an adult website, and when the email recipient visited the website, the malware installed itself, took over the webcam of the recipient’s device and began recording the recipient along with what they were watching. That footage, according to the email, is now in the scammer’s possession. Pay up (via Bitcoin) or the footage goes to all your friends, claims the email.
The scammers are bluffing, of course. But the scammer is hoping that the recipient may just have visited an adult website in the not-too-distant past, and may be naive enough to believe their claims. It’s extortion.
Sponsored Content. Continued below...
And those extortion emails may have just started to get even more convincing, because it seems that many of the crooks behind these emails are now also in possession of a batch of leaked passwords from one of the many security breaches to have hit large companies over the last several years. And instead of trying to ‘hack’ your online accounts using those passwords, the crooks are adding authenticity to their “you’ve watched adult content” email scams by including the passwords in the email itself.
So basically, the scammers are saying “you know we’re the real deal, because here is your password: XXXXXX“.
These passwords appear to have been obtained through security breaches that happened years ago. In at least one instance, the password was linked to dating app Zoosk (Zoosk has denied they suffered a breach) while others are likely to have been linked to more high profile security breaches such as the 2013 MySpace security breach.
Sponsored Content. Continued below...
Since most of the passwords appear to have been acquired through old security breaches, they may very well be old and out-dated passwords. But the scammers are hoping one of two things will happen –
1. The recipient hasn’t change their password and consequently believes the email, or
2. The recipient recognises it as an old password, but this is alarming enough to still convince them that the scammer is telling the truth.
Below is an example of such an email (we’ve redacted the email and password)
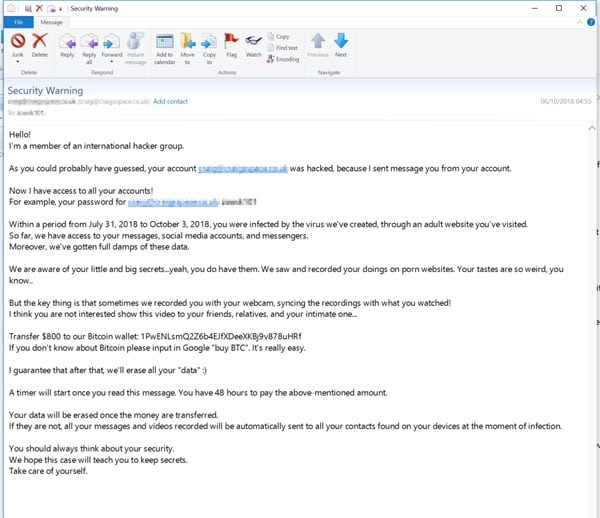
It’s likely that such emails are sent to thousands, if not millions of recipients. It’s likely that the leaked passwords were made available with their corresponding email addresses, meaning the scammers already had a mailing list.
The take away from this is that even if the extortion email lists a password, there’s a very high chance that the password was taken from a data breach, and has nothing to do with installing malware on adult sites to catch you “in the act”.
It goes without saying that if the password in the email is still in use on any of your accounts, change it immediately.
Keep up-to-date with all the latest cybersecurity threats and our tips to stay safe online. Follow us on Facebook, Instagram and Twitter.
Continued below...
Thanks for reading! But before you go… as part of our latest series of articles on how to earn a little extra cash using the Internet (without getting scammed) we have been looking into how you can earn gift vouchers (like Amazon vouchers) using reward-per-action websites such as SwagBucks. If you are interested we even have our own sign-up code to get you started. Want to learn more? We discuss it here. (Or you can just sign-up here and use code Nonsense70SB when registering.)
Become a Facebook Supporter. For 0.99p (~$1.30) a month you can become a Facebook fan, meaning you get an optional Supporter Badge when you comment on our Facebook posts, as well as discounts on our merchandise. You can subscribe here (cancel anytime.)
