What is Distributed Denial of Service (DDoS) attack? Jargon Buster
We explain what a DDoS (Distributed Denial of Service) is, how it works and how you can help prevent them from happening.
The notorious DDoS attack is a popular type of Internet attack that has long been a popular choice in the cybercriminal’s arsenal; it is frequently used to disrupt the websites and online services of a range of different companies, from small independent companies to large worldwide brands.
What is a DDoS attack
DDoS stands for Distributed Denial of Service. A DDoS attack essentially means those behind the attack will throw an incredibly large amount of information at a particular service (e.g. a website) with the intention of overwhelming that website or service resulting in it crashing and rejecting visitors. The information being sent to the website is often useless, arbitrary information that’s only purpose is to waste the website or service’s resources.
How DDoS attacks work
If you were to use an analogy in the offline world, it’s like sending thousands and thousands of people (the useless information) to a small coffee shop (the website) that have no interest in buying coffee, but will still sit on the tables, use the toilet and stand at the counter. Of course these people will be of no value to the coffee shop since they’re not buying anything, but there are so many of them that real customers cannot even get through the door!
Sponsored Content. Continued below...
Of course in the offline world, the coffee shop owner may very well call the police to get rid of all those people. On the Internet, it’s not that simple. The information getting directed to the website are real visitors, and it can be hard to determine who is behind the attack, or where the information is coming from.
DDoS attacks rely on the volume of information being so large that it overwhelms the website. And when you consider many of the websites that get taken offline because of DDoS attack are themselves very large sites capable of hosting large amounts of traffic and visitors, the volume of information needed to overwhelm them has to be incredibly large.
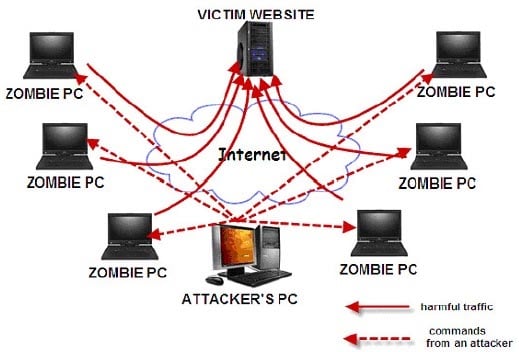
Explaining how a DDos attack works
This means one computer orchestrating a DDoS attack is not enough. The criminals have to utilise hundreds – maybe thousands – of different computers to orchestrate such an attack. This is where a “botnet” comes in. A botnet is a network of computers infected with malware that allows the crooks to control them. The crooks harness the combined processing power of all these computers (known as “zombie computers) under their control to initiate a DDoS attack.
In most cases, the owners of these zombie computers may not even realise they are infected and their devices are being used in this way.
Sponsored Content. Continued below...
Large botnets are capable of sending vast amounts of information to a particular source. DDoS attacks are not considered by security experts as a particularly high-tech form of attack, since it primarily involves simply flooding a service with information, but they are annoying nonetheless and cost businesses millions of dollars each year. They are also difficult to stop.
Lots of tools are available online where anyone can “hire” a botnet with a variety of DDoS attack tools, meaning they are a common occurrence online. And because the information used to flood a website comes from so many different sources, it can be hard to block the traffic since it isn’t as a simply as just blocking a specific address, and it can be difficult for victims to differentiate between genuine visitors and the useless traffic being sent as a result of the attack.
How can you help prevent a DDoS attack?
You can do your part to help prevent a DDoS attack by simply ensuring that all of the computers that you own (or are responsible for) are malware free. Criminals often rely on zombie computers to orchestrate an attack since they do not own the computing power to carry on out with just the machines under their control.
If botnets of infected computers did not exist because the public were collectively ensuring their computers were not infected, this would seriously limit the “firepower” that criminals could harness to carry out such attacks.
So, make sure each computer you own is malware-free by running a system scan with your up-to-date antivirus software. Which of course we know you do already because you’re a visitor to ThatsNonsense.com!
Stay safe out there.
Keep up-to-date with all the latest cybersecurity threats and our tips to stay safe online. Follow us on Facebook, Instagram and Twitter.
Continued below...
Thanks for reading! But before you go… as part of our latest series of articles on how to earn a little extra cash using the Internet (without getting scammed) we have been looking into how you can earn gift vouchers (like Amazon vouchers) using reward-per-action websites such as SwagBucks. If you are interested we even have our own sign-up code to get you started. Want to learn more? We discuss it here. (Or you can just sign-up here and use code Nonsense70SB when registering.)
Become a Facebook Supporter. For 0.99p (~$1.30) a month you can become a Facebook fan, meaning you get an optional Supporter Badge when you comment on our Facebook posts, as well as discounts on our merchandise. You can subscribe here (cancel anytime.)
