Malicious Email Attachment scams. How They Work
Emails that contain harmful attachments that when opened have the ability to infect a device are a popular way for cybercrooks to spread their malware, especially ransomware.
The email itself is sent to a recipient along with an email attachment, and if the recipient can be persuaded to open the attachment, that can lead to a malware infection. The challenge for cybercrooks is to somehow persuade a recipient that they need to open the attachment, and this is called social engineering.
Social Engineering
The social engineering aspect of any malicious email attachment scam is by far the most important. After all, if a person receives an email that is blank, or ones that says the attachment is a virus, that person probably isn’t going to open the attachment!
The cybercrooks needs the recipient to believe two things. That the email is legitimate and can be trusted, and that they need to open the email attachment. A crook’s ability to do this is called social engineering. Social engineering techniques can vary, but their objective is exactly the same. To lure an email recipient into opening an attachment and infecting their computer.
Sponsored Content. Continued below...
Popular Types of Social Engineering
It is impossible to offer an exhaustive list of different social engineering tricks used by scammers since there are so many, with new ones popping up almost every day.
However, common social engineering tricks can manipulate recipients by employing panic, urgency or piquing a recipient’s curiosity in order to lure them into opening an attachment. Additionally, we can provide some examples frequently used by scammers that also offer real-world examples of how social engineering tricks work.
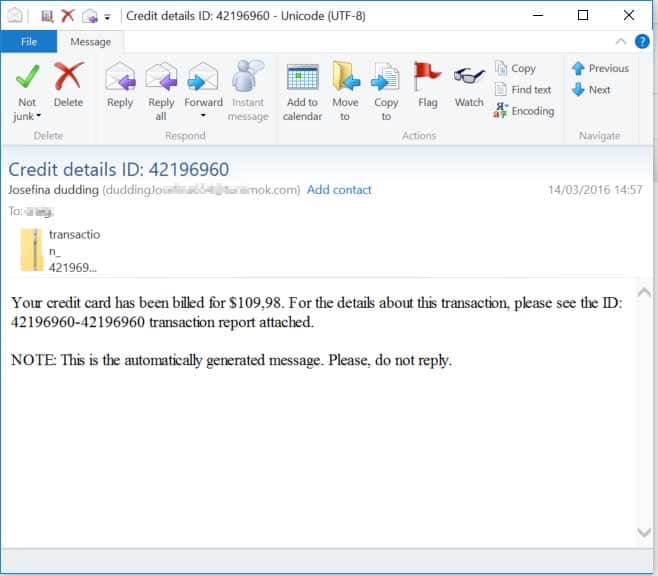
Bills, Invoices, Receipts or Purchase Orders
Emails may claim you’ve made a purchase or order, and to review that order you can open the attached invoice, receipt, order or bill. The trick is to alarm the email recipient into believing they’ve been charged for something they did not order. Alternatively if a recipient did make such a purchase, they may open the attachment since they may have been expecting an invoice. Example below.
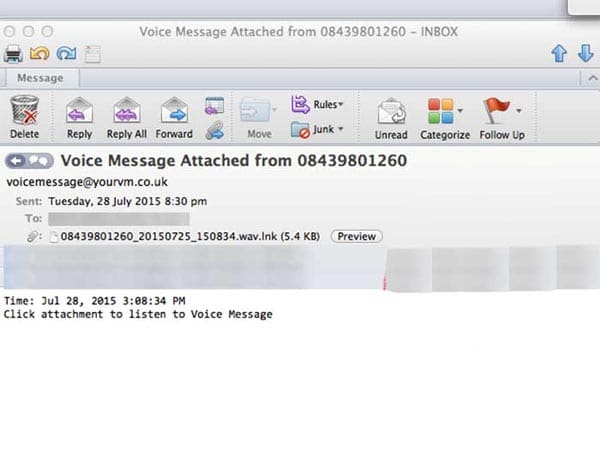
Voice Messages
An email may claim a voice message has been left for the recipient, who can listen to the message by opening the attachment. Example below.
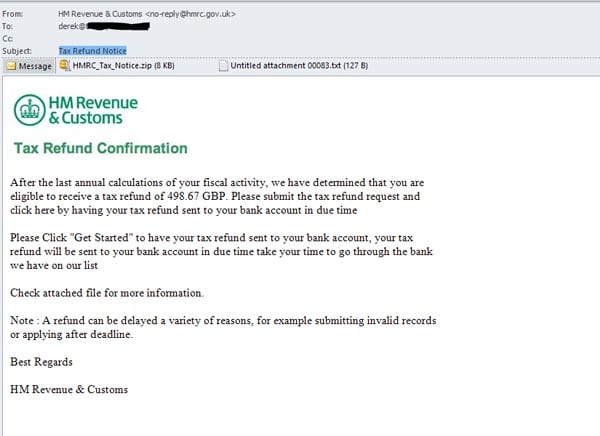
Prizes, Lottery Winnings, Rebates or Refunds
Emails promising a recipient money or some type of rebate may request recipients open an email attachment in order to see details about their winnings or rebate. Popular variants of this include the claim that the recipient is due a tax rebate or that they have won a lottery. Example below.
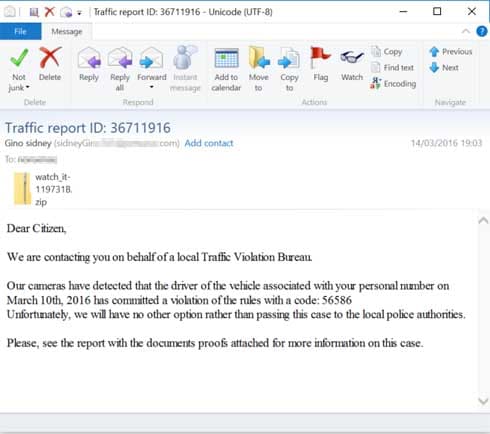
Complaints, Fines or Threats of Arrest
Emails threatening the recipient with fines or threats of arrest, or that a complaint has been made against the recipient, are designed to panic the recipient into opening an attachment to get more details. See an example below.
Types of Dangerous Email Attachment
Direct malware
The simplest and most direct type of dangerous email attachment, it is the attached file itself that is the malware. This can be in the form of a .exe file, .msi file or .iso file, for example. Opening the attachment is enough to infect a device with malware. However, this type of attachment is also the most likely to be spotted by security software either on a victim’s device or when travelling across cyberspace, so crooks often use other techniques to obscure the malware, discussed in the points below.
ZIP files
In this case, the attachment is “zipped”, meaning it contains a file(s) that is compressed, but that file cannot be seen until it is uncompressed. Such attachments are less likely to be caught by security software, but they require a recipient to both uncompress the ZIP file and then open the file inside for a malware infection to be successful.
Microsoft Word “macros”
MS Office documents (e.g. Excel and Word documents) are increasingly used to transport malware, because of macros. These are small pieces of code written by third parties that can be embedded in an Office document, and can infect a device with malware when the Office document is opened. This method of infection will require a user to both open the attached Office document and then enable macros (which are disabled by default for security reasons.)
Attached webpages
Less common are email attachments that are webpage documents, that simply direct a recipient to a webpage on the Internet. This webpage can then attempt to lure a recipient into downloading harmful files.
Sponsored Content. Continued below...
I Accidentally Opened a Scam Email Attachment
It is unlikely you were infected if…
– You opened an Office document, but did not click “enable content”, then
– You opened a ZIP folder, but did not open the file inside it.
– You visited a webpage, but did not agree to download anything from that webpage.
However, if you did do any of the above, or believe you opened a malicious attachment and are worried it may have infected your device, you should run a full scan with your antivirus software. (Our recommendations here.)
Avoiding Malicious Email Attachment scams
- Don’t open email attachments in unexpected emails. Even if the email looks legitimate or appears to come from a trusted source like a business or friend, it can still be a scam.
- Always check with the sender first. If you know the person who sent the email, contact them over the phone or in person to ask if they really did send an email to you with an attachment.
- If you open an Office document such as an Excel or Word file, don’t “enable content” (Macros) unless you are completely confident the Office document is genuine. This means not clicking on the “enable content” message displaying in the Office document when it opens.
- Have good security software installed on all your devices. Our recommendations are here.
Keep up-to-date with all the latest cybersecurity threats and our tips to stay safe online. Follow us on Facebook, Instagram and Twitter.
Continued below...
Thanks for reading! But before you go… as part of our latest series of articles on how to earn a little extra cash using the Internet (without getting scammed) we have been looking into how you can earn gift vouchers (like Amazon vouchers) using reward-per-action websites such as SwagBucks. If you are interested we even have our own sign-up code to get you started. Want to learn more? We discuss it here. (Or you can just sign-up here and use code Nonsense70SB when registering.)
Become a Facebook Supporter. For 0.99p (~$1.30) a month you can become a Facebook fan, meaning you get an optional Supporter Badge when you comment on our Facebook posts, as well as discounts on our merchandise. You can subscribe here (cancel anytime.)