New malware campaign disguises itself as presidential election email
Email users should be on the lookout for a number of convincing email malware scams that disguise themselves as “call to action” emails for the upcoming 2020 presidential election.
It is not uncommon for email scams to use events such as presidential elections as bait to trick recipients into opening malicious attachments or clicking on links to malicious websites.
With only weeks to go until the election, crooks are fashioning scam emails to appear to have come from the Democratic National Committee (DNC) asking for volunteers to help with campaigning, and urges recipients to open an attached Microsoft Word attachment. See the screenshot below.
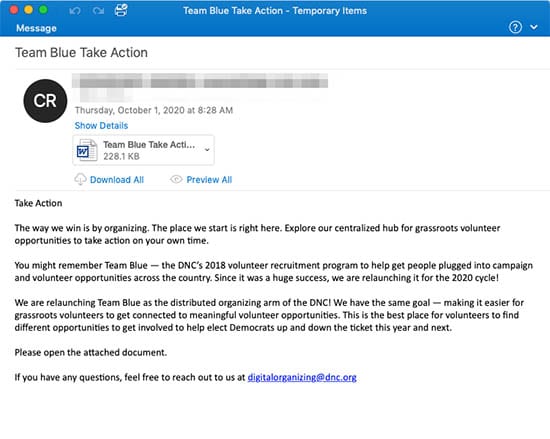
However, opening Microsoft Word files attached to emails can be a potential way of infecting devices with malware, and that is because of small computer files that Word uses called Macros. Macros are small files that contain code written by third parties; third parties that can, potentially, be cyber crooks.
Microsoft disables Word documents from automatically using these potentially dangerous macros, and instead will offer a user the option (via a dialog box) of enabling macros when they open a Word document. However, most users will not realise that enabling macros can be dangerous, and may agree to let them run without knowing the security implications.
Sponsored Content. Continued below...
If a user does agree to enable macros, these can download malware onto the user’s computer, infecting it with malware. In the case of this malware scam, that malware is called Emotet, which is a banking Trojan that can do any number of malicious activities on a device it infects, such as stealing financial information, executing ransomware or allowing crooks to take control of a device as part of a botnet.
According to researchers at ProofPoint, the emails in this malware campaign can contain the subjects
– Team Blue Take Action,
– Valanters 2020,
– List of works,
– Volunteer.
The Word document will typically be the same as the subject of the email.
Sponsored Content. Continued below...
When opening, the document will urge the recipient to “Enable Content”, which is Word’s way of asking users to enable macros, which then work to infect the device.
The email itself contains several paragraphs that have simply been lifted from the DNC website, making the email scam very convincing.
The advice is always the same. Don’t open email attachments from unexpected emails, and certainly don’t enable “content” (i.e. macros) on Microsoft Office files you were not expecting. The same goes for clicking on links in emails as well. And again, always run reliable security software on your computer at all times.
Keep up-to-date with all the latest cybersecurity threats and our tips to stay safe online. Follow us on Facebook, Instagram and Twitter.
Continued below...
Thanks for reading! But before you go… as part of our latest series of articles on how to earn a little extra cash using the Internet (without getting scammed) we have been looking into how you can earn gift vouchers (like Amazon vouchers) using reward-per-action websites such as SwagBucks. If you are interested we even have our own sign-up code to get you started. Want to learn more? We discuss it here. (Or you can just sign-up here and use code Nonsense70SB when registering.)
Become a Facebook Supporter. For 0.99p (~$1.30) a month you can become a Facebook fan, meaning you get an optional Supporter Badge when you comment on our Facebook posts, as well as discounts on our merchandise. You can subscribe here (cancel anytime.)

