The Colonial Pipeline ransomware attack explained.
The biggest headline in cyber-security news this week is about the ransomware attack on the Colonial Pipeline in the United States that serves 45% of the US East Coast’s fuel supply. We discuss what happened.
The attack is one of the most significant attacks on critical national infrastructure within the United States and another escalation illustrating how serious the problem of organised ransomware gangs have become.
While we may think of the fuel industry as a series of large pipes carrying dark viscous liquid from one place to another, the industry is actually a carefully digitised operation. An army of thermostats, gauges and even ‘smart robots’ control the complex system of pipes to ensure everything is running smoothly. And is often the case, it’s all connected to a central network.
It was that central network that was recently infected by ransomware. The infection resulted in the pipeline being shutdown, affecting the fuel supply of Alabama, Arkansas, District of Columbia, Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas, and Virginia.
This in turn led to the FMCSA issuing a state of emergency for those states.
Sponsored Content. Continued below...
It’s not known exactly how ransomware managed to access the network of the Colonial Pipeline. However like most other business networks, the administrative side is likely populated by employees using software most of us are familiar with, including the Windows operating system.
It’s likely that this is what the attackers targeted. It could have all come down to something as simple as an employee opening an email attachment they shouldn’t have (which is why it is so important for businesses to begin training their employees about computer security and not opening email attachments.)
The ransomware that attacked the Colonial Pipeline belongs to a criminal gang known as DarkSide. The DarkSide ransomware is an RaaS (ransomware-as-a-service.) This means it’s a strain of ransomware that is hired out by its developers (DarkSide) to other criminal gangs who select the target and typically initiate the attack. In this case the target was the pipeline.
Sponsored Content. Continued below...
The attack is one of the most serious ransomware attacks to date, but it appears the DarkSide ransomware gang themselves may have felt this attack may have went too far. In a statement issued by the group, they claim they will begin ‘moderating’ and ‘checking’ potential targets before an attack is initiated. They also claim their objective was to make money, not cause detrimental ‘social consequences’.
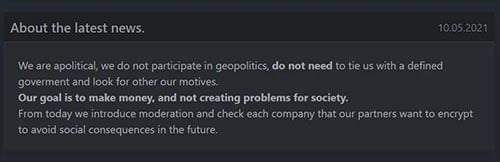
It’s possible, given this statement, that the DarkSide ransomware gang wasn’t happy with the target that was presumably chosen by the criminals that hired their ransomware. It does, after all, put them very much in the crosshairs of US law enforcement.
If this is the case, it is also possible that the decryption key will be released to staff at the Colonial Pipeline for free and no sensitive information that may have been stolen as a result of the attack released.
Whatever the outcome, this incident is a worrying escalation in the evolution of ransomware and the organised cyber-criminal gangs behind it that have created a complex digital ecosystem with the sole intention of profiting from malware.
Keep up-to-date with all our latest articles. Follow us on Facebook, Instagram and Twitter.
Continued below...
Thanks for reading! But before you go… as part of our latest series of articles on how to earn a little extra cash using the Internet (without getting scammed) we have been looking into how you can earn gift vouchers (like Amazon vouchers) using reward-per-action websites such as SwagBucks. If you are interested we even have our own sign-up code to get you started. Want to learn more? We discuss it here. (Or you can just sign-up here and use code Nonsense70SB when registering.)
Become a Facebook Supporter. For 0.99p (~$1.30) a month you can become a Facebook fan, meaning you get an optional Supporter Badge when you comment on our Facebook posts, as well as discounts on our merchandise. You can subscribe here (cancel anytime.)
